CKAN Turns 20: Two Decades of Open Data Infrastructure
CKAN turns 20. Explore how an open-source experiment became global data infrastructure, powering governments, research, and public-interest data worldwide.
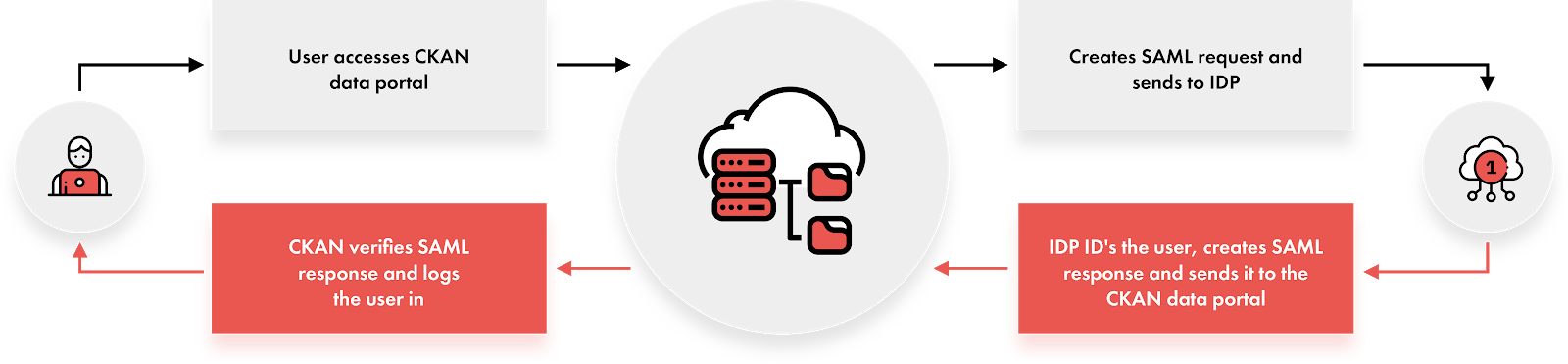
At the end of 2020, Keitaro’s team created and released ckanext-saml2auth, a CKAN extension that enables Single Sign On (SSO) for CKAN data portals via SAML2 Authentication. It works with CKAN 2.8 (ckan-2.8 branch) and 2.9+ (main), and can easily be installed on an existing CKAN data portal.
Many identity and access management (IAM) or access control solutions provide single sign-on (SSO). Verifying a user’s identity is important for determining which permissions each user should have. Single sign-on is a technology that integrates multiple diverse application login screens into one. With SSO, a user has to insert their login credentials just once on a single page in order to access all of their SaaS applications. SSO is generally considered to be more reliable, in regard to it being simpler and more convenient for users.
The ckanext-saml2auth extension is enforced by SAML2 Authentication, which is an XML-based open-standard for transferring identity data between two parties: an identity provider and a service provider. The identity provider performs authentication and passes the user’s identity and authorization level to the service provider. The service provider trusts the identity provider and authorizes the given user to access the requested resource. The ckanext-saml2auth extension works with CKAN 2.9+ and can easily be installed on an existing CKAN data portal.
The home of the U.S. Government’s open data, data.gov, adopted ckanext-saml2auth extension on their portal. By using ckanext-saml2auth, data.gov’s users are now able to use the benefits from it in day-to-day business and focus on their mission to improve public access to high value, machine readable datasets.
Data.gov is the U.S. government’s open data portal and is powered by CKAN. The aim of the portal is to improve public access to high value, machine readable datasets. It provides data, tools, and resources to conduct research, develop web and mobile applications, design data visualizations, and more.
By adopting the extension, data.gov’s users can save time, login faster and don't need to worry at all about the safety of their accounts. Explained in more details, the extension provides the users with:
If you want to install ckanext-saml2auth to your own CKAN portal, follow the instructions below:
sudo apt install xmlsec1
. /usr/lib/ckan/default/bin/activate
pip install ckanext-saml2auth
pip install ckanext-saml2auth
sudo service apache2 reload
# Specifies the metadata location type # Options: local or remote ckanext.saml2auth.idp_metadata.location = remote # Path to a local file accessible on the server the service runs on # Ignore this config if the idp metadata location is set to: remote ckanext.saml2auth.idp_metadata.local_path = /opt/metadata/idp.xml # A remote URL serving aggregate metadata # Ignore this config if the idp metadata location is set to: local ckanext.saml2auth.idp_metadata.remote_url = https://kalmar2.org/simplesaml[...] # Path to a local file accessible on the server the service runs on # Ignore this config if the idp metadata location is set # to local and metadata is public ckanext.saml2auth.idp_metadata.remote_cert = /opt/metadata/kalmar2.cert # Corresponding SAML user field for firstname ckanext.saml2auth.user_firstname = firstname # Corresponding SAML user field for lastname ckanext.saml2auth.user_lastname = lastname # Corresponding SAML user field for fullname # (Optional: Can be used as an alternative to firstname + lastname) ckanext.saml2auth.user_fullname = fullname # Corresponding SAML user field for email ckanext.saml2auth.user_email = email
A number of other optional configuration parameters are available and documented on the repository. That’s it. If you need any help setting up the SAML2 plugin, reach out to Keitaro’s team at info@keitaro.com.
Note: This post was written by Keitaro, you can see the original post on the Keitaro blog.
CKAN turns 20. Explore how an open-source experiment became global data infrastructure, powering governments, research, and public-interest data worldwide.
A recap of CKAN Monthly Live #39 covering POSE Phase II updates, the two upcoming storytelling workshops, a preview of the CKAN Ecosystem Catalog, and how the community can plug into CKAN@20 anniversary activities in 2026.